Perfect Info About How To Detect Keylogger Programs
Definition and types effective use of ai to speed malware detection definition of.
How to detect keylogger programs. These programs are adept at scanning your system for a range of. This process is called “logging”, and it allows. Press the windows key, type “control panel,” and press enter to open the control panel.
The answer is, it depends. Open your task manager using the windows search tab or pressing the ctrl + shift + escape keys. Fortiguard labs threat intelligence what is a keylogger?
Detecting a software keylogger can take more time. Leverage antivirus programs: Keyloggers are a famous tool hackers use to obtain passwords and other sensitive data.
Just look at the back of your computer and check for any unusual devices in your usb ports or connected to your keyboard cable. How to detect a keylogger? In this article we explore how to detect keylogger activity in your computer system by taking a quick look at some ways to counteract these problems.
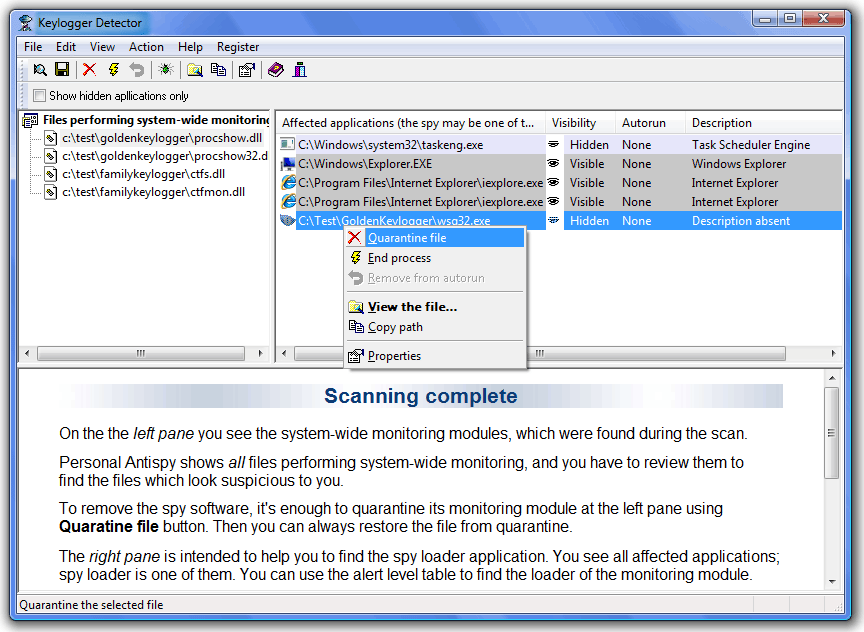
One of the simplest solutions to removing a keylogger is to uninstall the program which is recording your keystrokes. A keylogger is a form of malware the attacker plants into your device to track or “log” your keystrokes on the keyboard. In this article, we explain what keyloggers are and how they work, how to detect keylogger activity, and how to remove keyloggers.
Legitimate programs may have a keylogging function which can be used to call certain program functions using “hotkeys,” or to toggle between keyboard layouts. This is something that we must do periodically, but also whenever we detect an anomaly in the. To fight off keyloggers, start by utilizing an antivirus program.
How to detect keyloggers? Just be sure that you aren't removing a legitimate usb adapter by mistake. How to detect and remove keyloggers.
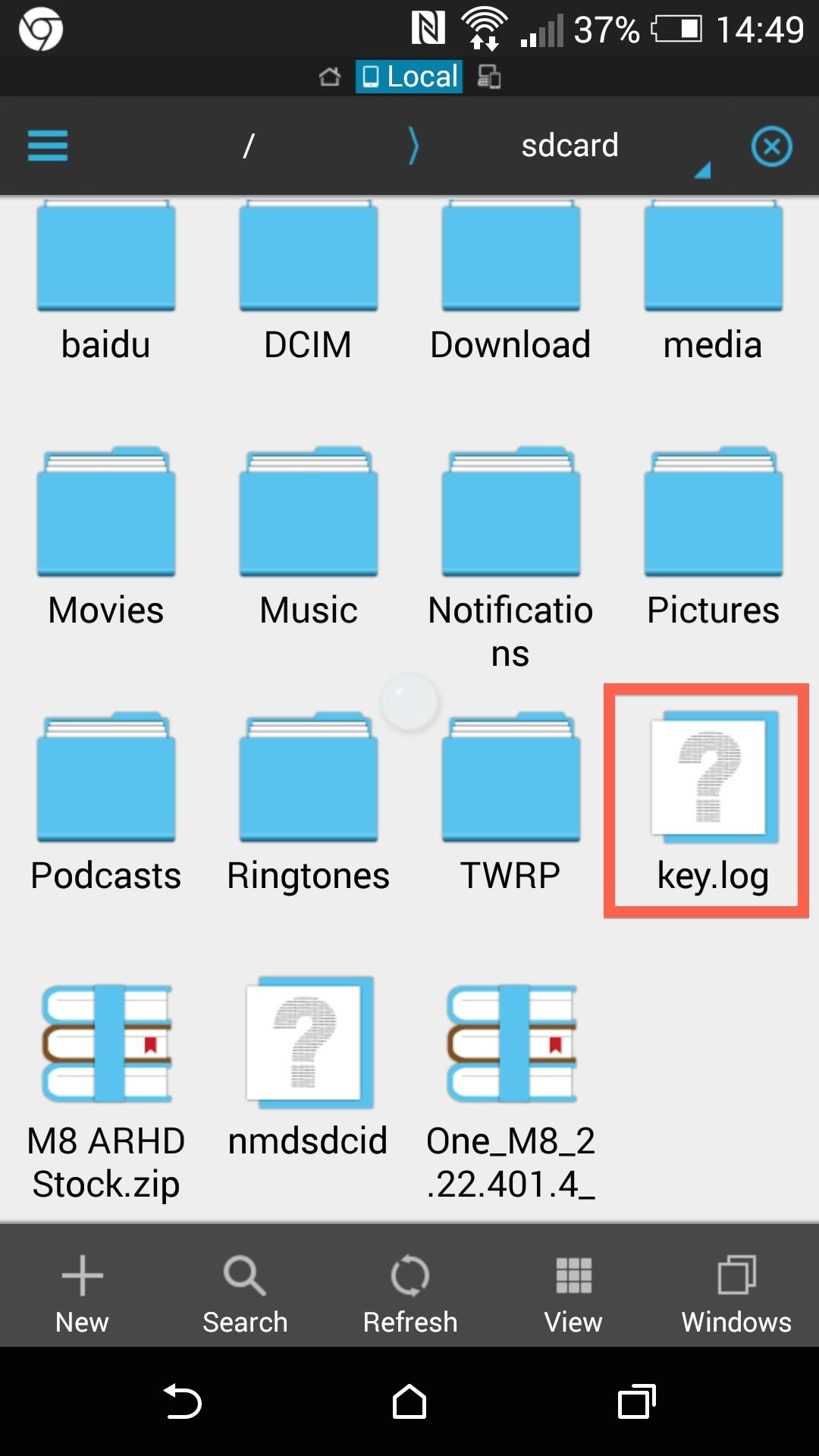
All they need is access to the device to detect keylogger in windows. How remove and prevent them from pc? Download now information captured by keyloggers when keyloggers run, they track every keystroke entered and save the data in a file.
Hackers can access this file later, or. Like most malware, you can use a good. Go through running processes even if the software program runs in the background, there must be a process running on the windows system.
How remove and prevent them from pc? Are there telltale signs that your device is hosting a keylogger? By aurelie | follow |.












![How to Detect a Keylogger on Windows [8 Solutions] Richannel](https://richannel.org/wp-content/uploads/2019/01/Installed-Programs-2.png)