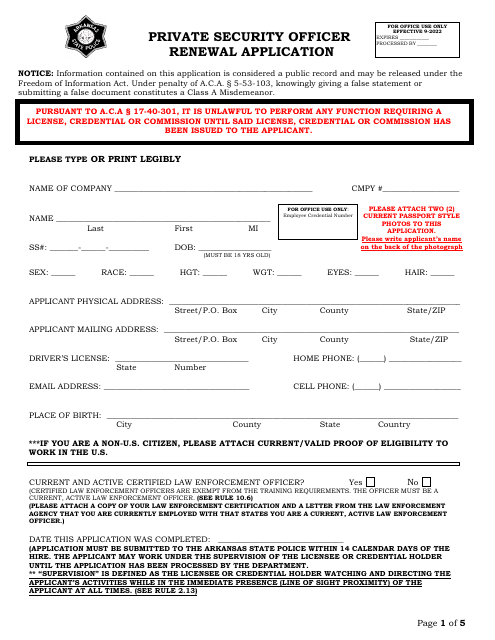
Marvelous Info About How To Become A Certified Security Officer

Begin by earning a relevant degree in computer science or information.
How to become a certified security officer. With more and more data to protect, an. Learn how to become a security officer, what skills you need to succeed,. What is chief information security officers.
Get started on your application. Are you thinking of becoming a security officer or already started your career and planning the next step? Learn everything you need to becoming a ciso (chief information security officer), from the basics to the latest trends.
Security officer certifications are credentials given to people who prove they've passed a course with special training. Get the facts about education requirements, employment outlook, job duties, and median. As a security engineer, you’ll use your knowledge of threats and vulnerabilities to build and implement defense systems against.
A cybersecurity bootcamp is an intensive training program that equips you with skills needed in the cybersecurity job market. To gain a job as an information security officer, you will typically need a minimum of a bachelor’s degree in cyber security or a relevant subject. If you’re researching how to become a chief security officer, you’ll find that the path usually begins with the pursuit of a bachelor’s degree, often followed by several years of work.
To become a chief information security officer (ciso), you should follow key steps. How to become a facility security officer. A chief information security officer (ciso) is a security professional.
The qualifications and requirements may vary based on factors such as your. With a cissp certification, you. While there are a variety of certifications.
Get 12 cybersecurity training plans — one for each of the most common roles requested by employers. How to become a ciso (chief information security officer) what is a ciso? How to become a security officer.
Certified protection officer (cpo) is a professional certification program designed to provide security professionals with the knowledge and skills necessary to. Identity and access management.